More actions
m →Skills |
|||
| Line 19: | Line 19: | ||
* {{sk|Hacking|price=yes|mult=yes}}: Required skill for the use of Data Analyzer modules. Gives +10 Virus Coherence per level. | * {{sk|Hacking|price=yes|mult=yes}}: Required skill for the use of Data Analyzer modules. Gives +10 Virus Coherence per level. | ||
** ''A la'' Archaeology, Data Analyzers require Hacking, and open structures found in Data Sites. {{sk|Hacking|I}} has slightly higher requirements than Archaeology I, but make sure you get both skills, so that you can hack any sites you find. | ** ''A la'' Archaeology, Data Analyzers require Hacking, and open structures found in Data Sites. {{sk|Hacking|I}} has slightly higher requirements than Archaeology I, but make sure you get both skills, so that you can hack any sites you find. | ||
** Also like Archaeology, higher skill levels make the Hacking minigame easier, and {{sk|Hacking|V}} will give you access to the Data Analyzer II module, which gives better bonuses, and is especially needed for Data sites | ** Also like Archaeology, higher skill levels make the Hacking minigame easier, and {{sk|Hacking|V}} will give you access to the Data Analyzer II module, which gives better bonuses, and is especially needed for Data sites in Nullsec or Wormholes. | ||
Some additional skills exist to make site location easier as you advance in your exploration career. | Some additional skills exist to make site location easier as you advance in your exploration career. | ||
Revision as of 21:10, 29 January 2015
The Odyssey and Kronos expansions to EVE Online took steps to streamline exploration in an effort to make it as easy an early money-making profession to get into as mining or mission running. While they did an admirable job, exploration can still be a bit daunting at first.
This guide is intended to provide new players with all the information they need to get started in exploring in high-security space. More experienced players who are new to exploration, or that have not explored since the Odyssey patch will find the sections on probing and hacking useful, as they are updated to contain information on the changes that were made to both systems.
Players will learn what skills are required to start exploring, what ships and equipment are best for the new explorer, what sorts of areas can be located using the exploration mechanics, how to use probes to track down hidden exploration sites, and how to use analyzer modules to hack into loot containers in exploration sites.
Getting Started as an Explorer
Skills
- Main article: Exploration skills
Much like mining, exploration doesn’t require a high skill level to get started. The three basic exploration-related skills follow.
- Astrometrics (3x, 500k ISK): +5% scan strength per level, −5% max scan deviation per level, −5% scan probe scan time per level
- Astrometrics allows you to use a Probe Launcher to launch (crazily enough) Scan Probes which you will use to locate hidden exploration sites filled with loot, enemies you can destroy, valuable gas clouds, or even wormholes to unknown parts of space!
- New characters start their career with Astrometrics I, but existing characters can easily obtain the skillbook from the Exploration tutorial missions.
- While exploration does not strictly require Astrometrics as much as it did pre-Odyssey, it provides useful bonuses and any serious explorer should plan to train to at least Astrometrics IV, which Astrometric Pinpointing requires.
- Archaeology (3x, 250k ISK): Required skill for the use of Relic Analyzer modules. Gives +10 Virus Coherence per level.
- Relic Analyzers require Archaeology, and are a fairly cheap mid-slot module used to interact with structures found inside exploration-located Relic Sites. A good amount of your income as an explorer will come from accessing these structures, so note this skill's importance!
- Higher skill levels make the minigame associated with opening Relic Site structures easier, with Archaeology V allowing you to use the significantly-more-powerful Relic Analyzer II module. Any serious explorer should plan to eventually max this skill out, especially if you intend to do Relic sites in Nullsec or Wormholes.
- Hacking (3x, 250k ISK): Required skill for the use of Data Analyzer modules. Gives +10 Virus Coherence per level.
- A la Archaeology, Data Analyzers require Hacking, and open structures found in Data Sites. Hacking I has slightly higher requirements than Archaeology I, but make sure you get both skills, so that you can hack any sites you find.
- Also like Archaeology, higher skill levels make the Hacking minigame easier, and Hacking V will give you access to the Data Analyzer II module, which gives better bonuses, and is especially needed for Data sites in Nullsec or Wormholes.
Some additional skills exist to make site location easier as you advance in your exploration career.
- Astrometric Rangefinding (8x, 500k ISK): +5% probe scan strength
- Astrometric Pinpointing (5x, 1M ISK): −5% maximum scan deviation
- Both these skills make it easier to track down difficult-to-find sites. You can learn and train a few levels of Rangefinding at the start of your career, but Pinpointing requires Astrometrics IV as a prerequisite, so you can wait and do it later.
- Astrometric Acquisition (5x, 1M ISK): −5% scan time
- Not as important at the start of your career, Acquisition speeds up how long a single scanning cycle takes—normally 10 seconds. Later on, when scanning in hostile territory, or attempting to probe for the location of an enemy ship, Acquisition becomes an important supplemental skill, but as a new explorer, patience suffices.
Ships
Any ship with a high slot can fit a Probe Launcher and start to explore. Keep this in mind as you advance in your career and start thinking about fitting ships to accomplish multiple tasks (i.e., explore in hostile territory, explore and complete any Combat Sites located).
However, a new explorer would benefit most flying a ship specifically designed for exploration: a Tech 1 Exploration Frigate. Each race has one.
- Gallente Imicus
- The Imicus has the best drone capabilities of any Tech 1 Exploration Frigate, making it a good choice if you’d like to use your exploration ship for some very light PvE duty.
- Minmatar Probe
- The Probe has enough mid slots for all the exploration modules you will want, plus 3 low slots for a defensive armour tank, or whatever other miscellaneous modules you think you may need.
- Amarr Magnate
- In a post-Odyssey world, the Magnate suffers a bit as an exploration frigate choice due to its limited number of mid slots, requiring it to make some tough decisions about what kind of equipment to take exploring, and what to leave back at the station.
- Caldari Heron
- The Heron mainly benefits from having 5 mid slots. As we will learn below, the standard fitting for a beginner’s exploration ship requires 4 mid slots, meaning that the Heron has an empty mid slot to further improve its exploration capabilities or defense.
All four ships give a 7.5% increase to scan strength of probes per Racial Frigate level, as well as a static +5 bonus to the Virus Strength of any Relic or Data Analyzers you fit. Each also gives a small bonus to Salvager cycle time, in case you occasionally use your ship to salvage wrecks. Useful bonuses all around!
At the end of the day, feel free to use whichever frigate you fly easiest (usually the one produced by your race), as they all run pretty closely in effectiveness.
Later in your career as an Explorer, you will likely move to the Tech2 version of the above ships (Helios, Cheetah, Anathema, Buzzard) which have slightly better bonuses, and can fit a Covert Ops Cloak; and much later, into your race's Tech 3 Strategic Cruiser with the appropriate Emergent Locus Analyzer subsystem installed.
The Sisters of EVE ships (Astero, Stratios, Nestor) have good exploration bonuses, better tank, and can fit the Covert Ops Cloak, but are much more expensive than the Tech 2 exploration frigates.
Equipment and Modifications
Probes and Probe Launchers
The key module required for exploration, the Probe Launcher, fits in a ship’s high slot. Probes and Probe Launchers come in several different varieties, but as a beginning explorer, you should only concern yourself with one type of each.
- Core Probe Launcher I
- Easy to fit, and does the job. It can only fire the most basic of probes, however, but this doesn’t hinder most explorers.
- Core Scanner Probe I
- The basic ammunition for the Core Probe Launcher. You can reuse them, and the Core Probe Launcher can hold eight at a time. You can technically locate an exploration site with as few as four, but for convenience, consider carrying at least one full reload (8), or even several reloads. This guide will assume you have at least 8 probes in your cargo hold at all times.
Both of these items each also come in a more expensive Sisters of Eve Faction version.
- Sisters Core Probe Launcher
- Provides a 10% bonus to scan strength of probes, but costs an exorbitant amount; as of January 2015, it sells for just around 45 million ISK at Jita. Alternately, it can be purchased directly from a Sisters of EVE loyalty point (LP) store for a combination of ISK (9.6 million) and LP (14,400). Once you're space-rich enough to afford it, it is well worth the cost.
- Sisters Core Scanner Probe
- Sisters probes have 10% greater scan strength than the garden variety Core Scanner Probes. They’re a bit expensive, but vastly more affordable than the Sisters launcher; as of January 2015, they sell for just over 535 thousand ISK each at Jita, or in a pack of 10 from the Sisters of EVE (1.2 million ISK + 1,800 LP for 10).
Consider looking into these as an upgrade once you’re starting to get the hang of exploration, but remember EVE Rule #1: don’t use them if you can’t afford to lose them!
Core Exploration Modules
In addition to your Probe Launcher for finding exploration sites, you’ll need a few core pieces of equipment in order to effectively plunder what you find for loot! These all fit in mid slots on your frigate.
- Relic Analyzer I and Data Analyzer I
- As mentioned previously, you’ll need these to access the loot structures in any Relic or Data Sites you find while exploring. You will definitely want both, and the vanilla Tech I version works perfectly fine at entry level.
- Cargo Scanner I
- When you arrive at an exploration site, you'll find multiple structures to analyze. Which one should you hack first? A Cargo Scanner will also tell you which structures in an exploration site have the most valuable loot, in advance. This becomes extraordinarily important if you get into a situation in which you’re competing with another explorer for the loot!
While the above three are “core” modules for running exploration sites, you are also strongly recommended to fit your ship with a 1MN Microwarpdrive module to make travel to and around scanned areas much easier. This makes a total of four mid slot modules—one more than the Amarr Magnate can slot. If you’re piloting one of those, you’ll have to make occasional decisions about which of these four modules to leave back at the station. In most situations, you’ll leave behind the Cargo Scanner or Microwarpdrive, but if you know for a fact that you'll only be exploring one type of site (Relic or Data), you can always temporarily forgo the Analyzer of the type that you won’t need.
Rounding Out Your Fitting
After fitting your Probe Launcher and exploration modules, you’ll have some space leftover for other equipment. What you choose here depends on your playstyle, but some general recommendations follow. The author also recommends that you take a peek at the Fitting Modules and Rigs Guide for more information on the sorts of options available to you here.
Cloaking
Most explorers will use a high slot to fit a cloaking device on their frigate: in this case, a Prototype Cloaking Device I. The topic of Cloaking goes beyond the scope of this article, and generally unnecessary for any high-sec exploration that you undertake, but keep it in mind for your future development as an explorer.
High-Sec PvE Combat
You may reasonably add a few modules to make your ship capable of handling some of the easier combat encounters that you’ll encounter while probing high-sec space. Specific fits will vary depending on your choice of frigate, but some options follow.
- Weapons
- You’ll likely have one or two high slots available for weapon turrets or missile launchers. None of the Tier 1 Exploration Frigates get bonuses to weapons, so use whatever weapon you have trained (generally tied to your race). Since Exploration Frigates don't slug things our well, consider longer-range options.
- An armor or shield tank
- Tanking goes beyond the scope of this article, but thankfully the University has good lessons in place already for both Shield Tanking and Armour Tanking. Equipping your ship with a few appropriate tanking modules will increase its survival rate if you decide to tangle with easier NPC targets. Note that you should never try to build both a shield tank AND armour tank on the same ship, and that shield tanking generally requires mid slots, of which your exploration kit already eats three. Beyond those caveats, a Shield Extender or some Armor Plates might make the difference between successful retreat and successful ejection from your freshly destroyed ship.
- A Salvager
- Salvaging the wrecks left by destroyed NPC ships supplements a new player’s income, so consider strapping a Salvager I module to your frigate if you intend to tangle with Combat Sites. Note that if you will only take your ship through non-Combat Sites (Data Sites and Relic Sites), you don’t need a Salvager. Some such sites did require a Salvager before Odyssey! You can find more info on salvaging at Salvaging 101.
- Drones
- Exploration Frigates have limited combat capability, but can all carry a payload of drones to make quick work of NPC frigates. The author advises you to carry a full Drone Bay of appropriate light scout drones any time you plan to run high-sec Combat Sites. Indeed, since they don’t cost much and have no downside to keeping them on hand, feel free to carry them anytime! Drones help in a wide variety of situations in Eve, so definitely give Drones 101 a read and learn more about these incredible little guys.
- If using drones, the author recommends a Drone Damage Amplifier to improve their offensive capability for a low-power slot.
Miscellaneous
- Several new mid slot modules exist that increase your scanning abilities: the Scan Acquisition Array, the Scan Pinpointing Array and the Scan Rangefinding Array. While you may wish to look into these eventually, they only recently entered the game and cost a lot—and more likely than not, you won’t have the mid slots open for them anyway!
- Low-slot Inertial Stabilizers, Nanofiber Structures, and Overdrive Injectors increase ship agility and speed. Speed always helps, as it makes maneuvering between exploration site structures easier, and makes it more likely for you to escape if something goes wrong. Of those three modules, Nanofiber Structures will probably benefit you most, as they raise several speed/agility related stats in exchange for a none-too-painful drawback.
- Alternately, a low-slot Expanded Cargohold will increase your cargo capacity by up to 20%, at the expense of velocity and structure HP. This can be useful if you're exploring far from home, and you'd like to cram in just a bit more loot before heading back to base.
Rigs
Of all rigs, you’ll most likely want to install the Gravity Capacitor Upgrade I, which increases probe scan strength by 10%. Fitting two Tech I rigs provides a greater improvement than a single Tech II rig, which works out great as a low-skill explorer.
If you're going to specialize in one of Relic or Data sites, then adding that rig also helps by giving you bonuses: Emission Scope Sharpener for Relic sites, or Memetic Algorithm Bank for Data sites.
Exploration Using Probes
The main object of an explorer is to track down hidden areas found in systems across all of the EVE universe. These areas contain valuable items or other points of interest, but cannot be warped to initially. Instead, a player must use their ship’s scanner and their Probe Launcher to track down the “signals” of these hidden areas through a process generally referred to as “probing,” or “scanning,” or “exploring.” If you’ve ever heard someone mention that they are going to “probe down a site”… this is it!
At this point, it is assumed that you are in an exploration ready vessel, much like the one outlined in the above section, and that you are packing a payload of at least 8 Core Scanner Probes.
A Good Place to Start
When you first begin exploring, you will likely want to stick to high-security space: systems with a security status anywhere from 0.5 to 1.0. You will be pretty safe in these systems, but there are some best practices you can start to follow so that they are routine as you move into exploring more dangerous space.
- Explore in quiet systems
- Pop open your Star Map and set it to look for “Number of players in the last half hour.” This will set your map to display large or small circles that indicate how much traffic a particular system has seen recently. In high-sec space, your biggest annoyance as an explorer will be other high-sec explorers: there are only so many exploration sites out there, and you will be racing other explorers for them. Areas with lots of traffic typically won’t have any exploration sites of interest to you, and the ones that do appear will likely be pounced on by someone else. Don’t get into a tug-of-war with other high-sec explorers: find a quiet stretch of systems somewhere and do your exploration there!
- Explore from a safe place
- While probing for exploration sites, your ship will be motionless for extended periods of time. This is dangerous in many parts of EVE. In high-sec, you will probably be perfectly safe idling some distance from a dockable station, or, say, 100km out from a planet. You will be even safer if you have a cloak fitted and activate it when you get to your spot. Indeed, you can explore cloaked so long as you remember to launch your probes first before engaging the cloaking device. In low-sec and other dangerous parts of space, you will want to explore from what's called a Safe Spot, and you will pretty much always want to be cloaked. You can find more info on locating and using Safe Spots in the Bookmarks lesson, and high-sec is a great place to get in the habit of using Safe Spots to explore unhindered!
- After finding a safe spot for your ship, an extra precaution you can take is to point your ship in a semi-random direction away from the system’s major points of interest and (if you're not cloaked) then activate your Afterburner or Microwarpdrive. You can safely do this while focusing the majority of your attention on your probing. This is very helpful if you are flying without a cloak: the forward momentum makes it harder for hostile players to track you down, and even if they manage to, you will have a head start on them and should be able to escape!
Checking Your Ship Scanner
You’ve found a quiet system to explore and are safely nestled in a comfortable spot. Cocoa and blankets are optional. Time to explore! Pop open your ship’s scanner using the little button on your ship’s HUD that has a picture of a radar screen on it (or press ALT-P). While you were parking your ship somewhere, your scanner was busy! It’s more than likely tracked down a few points of interest throughout the system. Note that if your scanner readout says “No Signals Detected,” that means the system is currently empty. Head to a different system to explore, but note that you can always come back to this system again later to see if anything juicy has appeared.
There are two types of signal that your scanner may have just picked up: Cosmic Anomalies and Cosmic Signatures.
Cosmic Anomalies
Cosmic Anomalies are areas of interest that radiate a strong enough signal that you can jump to them immediately after your ship scanner finds them. You don’t need to do any fancy probing or anything: just click and go! Of course, since everyone can easily see these sites, they’re typically less rewarding, and possibly more crowded than Cosmic Signatures.
Cosmic Anomalies come two main flavors...
- Combat Sites
- Regular versions of these sites are a single area filled with several waves of NPC opponents. Blow them up for bounties and loot! Check the Cosmic Anomalies page for information on the general difficulty of these sites. If you built the High-Sec PvE Combat frigate outlined earlier, you should be able to handily deal with Cosmic Anomalies of the lowest two difficulties (Burrows and Hideaways).
- A special kind is a Covert Research Facility
- If the tag is Lesser/Standard/Improved/Superior, then these are Ghost Sites, which have NPCs and hacking. They can be run with good skills, and sufficient tank (usually a cruiser). Before attempting these, see Ghost Site for a lot more details.
- If the tag is "Besieged", then these are serious Combat sites, that contain a bunch of NPCs including Mordu's Legion Battleships! As an explorer, avoid these at all costs!
- Ore Sites
- These sites are temporary pockets filled with either ice asteroids, which can be mined for fuel components, or regular asteroids of a rarer type not normally found in that system. You can tell what kind of asteroids are within the site by the site’s name: they’re pretty obvious. These can be interesting places to head if you’ve cross-trained as a miner, but remember, because they are so easily found, they will likely be filled with other pilots, both friendly and less so.
Cosmic Signatures
Cosmic Signatures are the bread and butter of an explorer. These are hidden areas that cannot be warped to unless tracked down by probes. Because of this extra step, Cosmic Signature exploration areas can be very lucrative, even in high-sec space!
When you first enter a system, none of its Cosmic Signatures will have any identifying information besides a generic designation, such as “MRM-213.” However, much like Cosmic Anomalies, Cosmic Signatures come in several types. You just won’t know exactly what you are tracking down until you pull out your probes!
- Combat Sites
- Combat Sites that are tracked as Cosmic Signatures are more complex than Cosmic Anomalies: indeed, they are complexes! Complexes are EVE’s version of “dungeons”. They are made up of several “rooms” of space connected by Acceleration Gates, and they frequently have containers filled with great loot. Of course, they are also guarded by large numbers of NPC ships. Cosmic Signature Combat Sites come in two general flavors, both of which are more difficult than the equivalent Cosmic Anomaly site: DED Complexes and Unrated Complexes. While the High-Sec PvE Combat frigate listed above might be able to clear the 1/10 difficulty version of these Combat Sites, you’re probably better off fielding a separate, combat-oriented ship to deal with them. Just probe down the site’s location, save it as a bookmark by right-clicking on it, then pilot a bigger, angrier ship in and enjoy! Or make friends by sharing the bookmark with others, and letting them run the combat site.
- Relic Sites
- Relic Sites are locations filled with abandoned structures filled with salvage and other loot. Best of all, in regular (non-wormhole) space, they’re filled only with valuables: no NPC defenders. Your exploration frigate can happily sail into these sites and use their Relic Analyzer on the structures within to pry out valuables. See more details below on the hacking minigame, and/or see Hacking 101.
- Data Sites
- Data Sites work exactly like Relic Sites, but they require a Data Analyzer to access. They contain valuable loot in hackable cans, and no NPCs. Items worth millions of ISK sometimes drop here even in high-sec, so keep a sharp eye out for them!
- Gas Sites
- Most high-sec Gas Sites are Nebulas, which are quiet, undefended areas that have several gas clouds that can be harvested with specialized, expensive equipment. Sadly, most high-sec gasses are not worth much ISK, either, meaning that most new explorers should avoid these sites. Gas Sites are more lucrative in lower-security space, which you likely won’t venture into at first.
- Occasionally, a Gas Site may be a Lab or other facility that pirates have set up to harvest the gas for themselves. These areas are a combination of Combat Site and Data Site, and contain hackable structures that are guarded by NPC opponents.
- Wormholes
- Wormholes are temporary gates that can take your ship from your current system to almost anywhere else in space, including dangerous “uncharted” areas referred to as “wormhole space” or “w-space.” W-space areas contain the most lucrative exploration sites in the game, but most of them are guarded by powerful Sleeper NPCs, even the Relic and Data Sites that are so tame in high-sec. (As of the Phoebe release in late 2014, nullsec Relic and Data sites with Sansha, Guristas, Angel and Serpentis in their names are unguarded sites in WH space. So after learning more about WH's, if you have enough data/relic skills, you could consider running these.) For these reasons, at the start of your career, you should leave wormholes alone... but don’t forget about them! Later articles will go into how you can begin dipping your exploration toe into the vast, untamed pond of wormhole space. See the Wormholes information page and the Wormholes 100 class for more detailed information.
Probing Down an Exploration Site
Your system has a few Cosmic Signatures listed, and you’re well versed in what could possibly be out there. Let’s probe one down.
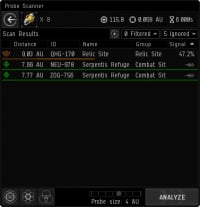
- You already have the scanning panel open, but let’s hit F10 to open up the Solar System Map. This is a “wireframe” representation of the system you are currently in, complete with all the major celestials, like planets, moons and the sun. Since you have your scanning window open, there should be some green and/or red dots and spheres on your map. These represent the Anomalies and Signatures currently tracked by your scanner, as well as their general location. Green dots indicate areas that you can warp to, either an Anomaly or a Signature you have scanned down. Red dots or spheres represent the general area in which your ship’s scanner is detecting the signal of a Cosmic Signature. We’re going to have to narrow that down in order to warp there.
- The middle left of your scanner window has an icon that looks a bit like an atom. That’s the shortcut for the “Pinpoint” probe formation. Press it, and your ship will launch its payload of probes and automatically arrange them in a Pinpoint formation. Neat!
- You should now notice that some blue spheres have appeared on your Solar System map. That’s the general area that your probes can currently scan. The center probe in this formation is represented by a white box with arrows sticking out of it. You can click and drag those arrows to move the probes around: by default, dragging that center probe will move all the probes together in formation. This is useful. Now, in order to start tracking down a Signature, you will need to drag your probes so they are centered over one of the red Signature dots or spheres and then press the Activate button on the middle left of your scanning window. This will scan that area more thoroughly with your probes, and will take a few seconds to complete. If the signature’s red sphere is larger than the area your probes’ blue spheres cover, click and hold the outside edge of one of the blue spheres and drag outward. This will increase the range of your probes so you can scan the whole red sphere. If all this is done correctly, the scan will complete and increase the Signal Strength of your chosen Signature. This is listed on the far right of your scanning window.
- The goal of probing is to increase a Signature’s Signal Strength to 100%. As you continue to increase the Signal Strength, you will begin to learn more and more about the Signature: first, what type of Site it is, followed by the specific name of the site, and then finally, the Signature’s actual location so you can warp to it! Obviously, this is why we’ve picked a ship and equipment that raises the scan strength of our probes: it makes it much easier to get this number to 100%.
- Now, it’s unlikely this first scan got the signal to 100%. In order to further increase its Signal Strength, we’re going to have to give our probes more power by reducing the range of their scan. We do this by clicking and holding the outside edge of one of the probe’s blue spheres and then dragging it inward. This will decrease the size of your scan. Now, re-center your probes on your signature’s dot or sphere and hit the Activate button again. If done correctly, your smaller scan area should still catch the Signature and will end up increasing its Signal Strength.
- Most Signatures can be probed down by repeating this process: reduce your scan range by a step, re-center your probes on the Signature, and scan! It’s just that easy.
- Once you’ve raised the Signal Strength to 100%, the Signature’s Signal Strength will turn into an arrow you can click to warp to the newly located Site. Congratulations! You’re exploring!
Probing Tips and Troubleshooting
- You may occasionally come across a Signature that refuses to hit 100%, despite the fact that you have your probes centered on it at their minimum range (0.25 AU). If this happens, there are a couple things you can try before giving up and resolving to raise your probing-related skills.
- Holding the SHIFT key down will allow you to maneuver individual probes, rather than your entire formation. If you are using the Pinpoint formation as recommended, you’ll notice that five of the probes are along the same plane, with four hovering around the outside of the center probe. Shift these four probes around the center probe so that they form a cross, with one probe at each cardinal direction. Activate your scanner again: this in and of itself may be enough to make the Signature warpable. If not, move the four probes closer to the center probe. You’ll want to get them pretty close, without having them overlap. Zooming your view in using the mouse wheel will help here. Alternate shifting the cardinal point probes closer and activating your scanner to see if this raises the Signal Strength enough.
- If the above isn’t quite enough to get the Signature to 100%, you can try shifting the entire formation of probes in a single direction a very small amount and then re-scanning. Since the dot that represents the Signature’s location isn’t 100% accurate until its Signal Strength is 100%, you can sometimes squeeze out an extra percentage point or two of Strength in this manner. This can be a bit tedious, however, as the margin for error is so small. It’s recommended that you only try this if you are painfully close to 100% Signal Strength!
- Note that as a new explorer, sometimes you’ll just plain be unable to scan a Signature all the way down to 100%. This is very unlikely to happen in high-sec space, but if it does, don’t let it get you down. Just remember, one day your skills and equipment will be good enough that no Signature will be able escape your grasp!
- After you’ve probed something down, you may notice that your scanner used to have a bunch of Signatures on it, but now does not. This is because launching probes and reducing their range has removed those Signatures from your scanning region. This is easy enough to remedy, however. You can either expand your probes’ range to their maximum and re-scan, or temporarily switch the Spread formation and re-scan a larger area. In both cases, make sure your probes are covering as large a space as possible: the entire system, if you can. That should find those missing Signatures easily!
- While scanning, once you have a signature down to a single dot, double-click the signature in the scanner window. This will center your star system map on the signature, and, more importantly, make the camera rotate around it (instead of around the sun), which makes moving and aligning your probes much easier.
Relic Sites and Data Sites: Hacking
You’ve managed to locate a Relic or Data Site. Half the work is done: now you just need to find the loot inside!

With the release of Phoebe in late 2014, regular Pirate-faction Relic and Data Sites also spawn in C1 to C3 wormholes (in addition to the Sleeper-guarded Data/Relic that have always been there). The quality of these sites are comparable to null sec. Phoebe also slightly buffed the drops from Data sites, per this dev blog.

Relic and Data Sites are set up very simply. They are pockets of space populated with a variety of cosmetic structures (i.e., wrecked stations, abandoned machines) and several containers that will always look the same, but be named differently. Data Site containers look a bit like an gyroscope, and typically have names like [Faction] Info Shard or [Faction] Com Tower. Relic Site containers look like ancient shipwrecks and have names like [Faction] Debris or [Faction] Rubble.
To see these containers on your overview make sure you have selected "Scatter Container". This can be found by opening overview settings, Filter tab, Types, Entity. They will show up with a diamond symbol, solid for not hacked and empty for hacked containers.
These containers hold all of the site’s valuables, but you can’t just fly up and take them: you’ll have to hack into the containers first by playing the Hacking/Archaeology minigame. In order to attempt a hack, you’ll need to lock on to the container, fly within 5000 m of it, and then use the correct module on it (your Relic Analyzer in a Relic Site, or your Data Analyzer in a Data Site). This will pop open a new window containing the hacking minigame.
Hacking Minigame
- Main article: Hacking 101
Mercifully, the hacking minigame is identical in both Data and Relic Sites, aside from a few cosmetic changes to the game’s playfield and sound effects.
The object of the hacking minigame is to find and disable the container’s System Core. You do this by maneuvering a virus through the board of “nodes” that represent the container’s electronics.
Moving around the board is easy enough. Unexplored nodes in the system are marked as green. Clicking on an unexplored node will reveal its contents: if the node is empty, it will turn orange and allow you to further explore nodes adjacent to it. Sometimes, however, a node will contain an obstacle or other item of interest.
A more recent (late 2014) addition is that as you click on each node, if it is unoccupied, it will briefly display a "minesweeper" number, from 1 to 5, which indicates the distance from the nearest good (or possibly good) node. (5 means "5 or more".) This shows distance from any undiscovered Utility Subsystem, System Core, or Data Cache (even though Data Caches are not always good). The numbers can be used to guide the direction that you should move around the grid.
Among the various things a node may contain are...
- Defensive Subsystems
- These are represented by large circles with an icon inside, and they will be the bane of your hacking existence. Defensive Subsystems prevent you from exploring adjacent nodes until they are disabled.
- Each Defensive Subsystem has two ratings: a Coherence, which is the equivalent of its health/HP, and Strength, which is equivalent to its “attack power.” Coherence is represented by an asterisk and is listed atop the Subsystem. Strength is represented by a “wifi/signal” icon and is listed at the bottom of the Subsystem.
- Thankfully, your virus has a Coherence and Strength, too, which you can use to disable the system’s defenses! You can attack a Defensive Subsystem by clicking it after it has been explored.
- Attacking a Subsystem is turn-based: your virus will attack the Subsystem, and then, if the Subsystem is still active, it will attack your virus back.
- Your virus’s Coherence and Strength are listed in the bottom left of the hacking window. When you attack a Subsystem, you will lower its Coherence by your Virus Strength. If you reduce its Coherence to 0, it is disabled and removed from the board.
- If your Virus Coherence reaches 0, you fail the hack and the window is closed. Failing a hack once will just make it less likely for you to get any valuable loot from the container (explained below), but attempting a second hack and failing again will destroy the container.
- Defensive Subsystems come in a few different types.
- Firewalls have high coherence, but low strength.
- Anti-Virus subsystems have low coherence, but high strength.
- Restoration Nodes show up in more difficult hacks. Each turn they are active, they will give extra coherence to all other uncovered defensive subsystems. Incredibly nasty.
- Virus Suppressor subsystems lower your Virus Strength while active.
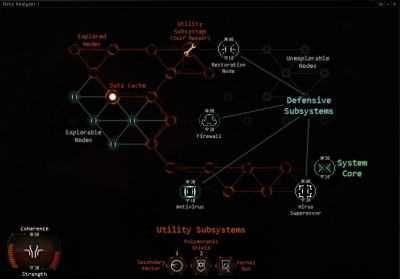
- System Core
- The System Core operates a lot like a Defensive Subsystem, with the major difference that disabling it will successfully complete the hack.
- The System Core typically has a lot of Coherence.
- Its icon looks like a “X” inside a Subsystem circle.
- The color of the System Core reflects the difficulty of the container: Green for easy; Orange for medium; Red for hard.
- Utility Subsystem
- Utility Subsystems are helpful, consumable “files” that have been left inside the system. You can click one once it has been exposed to add it to a utility slot at the bottom middle of your hacking window. They can then be used by clicking the appropriate utility slot. You can only store three Utility Subsystems at a time, so plan ahead!
- Utility Subsystems are extremely useful and come in a few different types.
- Self Repair utilities increase your Virus Coherence by a variable amount. A single Self Repair has three “charges”: the first is consumed immediately after use, and the next two are automatically used after your next two actions in the system (i.e., exploring a node, attacking a subsystem). Always use a Self Repair as soon as you find it - there is no gain in waiting.
- Kernel Rot utilities reduces a target subsystem’s Coherence by 50%. Great for use on the System Core.
- Secondary Vector utilities reduces a target’s Coherence by a variable amount. Much like the Self Repair utility, the Secondary Vector has three charges: one used immediately, and two more that fire off after taking actions.
- Polymorphic Shield utilities prevent the next two instances of damage done to your virus. Good for taking down subsystems with high Strength.
- Data Caches
- Data Caches act a bit like a “treasure chest.” They can contain either a “treasure” (a useful Utility Subsystem), or a “trap” (a particularly nasty Defensive Subsystem). Data Caches have to be manually opened after being exposed (single-click them), so you can safely leave the decision as to whether or not to chance their activation until later on in your hacking attempt.
Thankfully, exploring until you find the System Core and then annihilating it isn’t too difficult in the vast majority of sites you will find in high-sec. With a little practice, you’ll be hacking with the best of them!
Hacking Tips and Tricks
- As a general rule, you’ll want to explore as many nodes as you can before attacking any static Defensive Subsystems. In general, it’s better to explore the entire board before engaging with any subsystems: you may just stumble onto the System Core early! Restoration Nodes and Virus Suppressors are the exception to this though, as they should be removed from the board as soon as possible.
- Always pick up Utility Subsystems as soon as they are exposed. If you keep exploring without snagging these, a Defensive Subsystem might pop up and cut off your access to them!
- Always use a Self Repair as soon as you find it. It simply increases your Coherence, so there is no gain in waiting.
- Don’t open Data Caches until you’ve fully explored all their adjacent nodes. You don’t want your exploration to be cut off by an unexpected Defensive Subsystem!
- Additionally, more difficult hacks contain Data Caches that might expose particularly nasty Defensive Subsystems (Restoration Nodes), so sometimes, you may just want to leave opening Data Caches as a last resort.
- Because exposed Defensive Subsystems cut off access to adjacent nodes, you may want to explore nodes along the edges first before exploring inward. This is because if you happen to expose a Firewall or Anti-Virus along a “wall,” you will be a bit less likely to cut off all of your movement options in that direction.
- Use the 1-5 "minesweeper" numbers in empty nodes to guide your movement around the grid. For example, if you're approaching an edge or corner of the grid, and the number is a 5, then trying to explore anything towards that corner/edge is not useful, because you know that there cannot be anything good within 5 nodes. In general, you want to click in directions that make the numbers smaller. Because the numbers disappear as you move along, you need to remember where there were 5's, so you know which areas not to bother going back to later.
Item recovery
Once you’ve successfully hacked the system, the loot is yours! Prior to the Kronos update in June 2014, explorers had to quickly collect the loot components from cans that spewed from the exploration structure into space, before they disappeared.
Thankfully, Kronos changed this so that hacked structures turn into simple, stationary containers that you can loot ("Open Container") at will. Data and Relic structures contain different types of loot (plus sometimes junk like Carbon):
| Items found in Data sites: | Items found in Relic sites: |
|---|---|
|
Decryptors |
T1 Salvage |
The most commonly dropped Skill Books are usually not that valuable, are typically one of the Rigging or <Race> Encryption Methods Science books.
Some of the rarer and more valuable Skill Books that can be dropped from Data sites are the <Type> Physics Science books.
The most commonly dropped BPCs are not worth very much, and include things like ancillary armor/shield reppers, micro jump drives, target spectrum breakers, etc.
The rarer and valuable BPCs can be Faction POS guns, and even Faction POS tower BPCs.
As always, the more difficult the site, and the more dangerous the location (high<low<null<WH), the better the loot you are likely to receive.
Survival
As with most things in Eve, the more dangerous the environment the higher the rewards. Exploration in HighSec tends to have low return on time, but the minigames are far easier and the risk of attack is far lower. As you start moving into more and more negative space the rewards begin to go up significantly. However, by the time you start running sites in null sec you will most likely want to have T2 modules and appropriate rigs for your exploration vessel. This will typically mean that you will be running sites in a ship that has little to no defensive or offensive capability beyond being fast and hopefully cloaky. You may also not have an opportunity to sell your loot frequently, this can lead to a cargo hold full of 100's of million of ISK in a hull that is paper thin.
Outside of high-sec, it is common for other players to scan you down, not just with the traditional combat probes, but with core scanner probes as well - since you will be in a scannable location. While running the site, and particularly while in the minigame, keep your overview and Local visible, and keep running D-Scan. If you see any probes zero in on you, move quickly away from the structure you are looting and cloak up or warp out. A well used Stealth Bomber, Recon ship, or T3 Cruiser, can make extremely quick work of you, and turn a nice profit in the process. Also keep in mind that somebody else may be there already and cloaked. Especially as you start interacting with the first structure - watch your Local and be ready to run fast. A cloaked stealth bomber could just be chilling waiting for you to start the minigame and lose situational awareness.
When on approach to a site you can make a nearby escape bookmark on your way in. This acts as a quick bugout location that lets you still keep a D-Scan eye on the site you are running to see who comes in.
Remember, even though you have invested in scanning down the site, and may be close to finding the system core, it probably isn't worth risking your ship and your cargo to finish a particular structure or site.
Also note - when running some sites in wormholes there will be Sleepers, and all of the above still holds except local won't help and the locals may have already scanned the site so may not need to drop probes on you (of course this can also hold true anywhere - but what's life without a little risk!)
