More actions
→Ships and equipment: Updated this section to be more similar to the Ships and Equipment section of Scanning due to their similarity. |
|||
| Line 84: | Line 84: | ||
===Ships=== | ===Ships=== | ||
Hacking can be done in any ship that has mid slots for Data and/or Relic Analyzers. However, there are ships with innate bonuses to hacking. | Hacking can be done in any ship that has mid slots for Data and/or Relic Analyzers. However, there are ships with innate bonuses to hacking. These ships gain very helpful bonus to hacking module virus strength, the additional probe strength bonus helps with scanning. Nothing prevents you from doing hacking in other ships but unbonused hull places more weight on skills and knowledge. | ||
Each race's T1 Exploration frigate has an innate role bonus of 5+ virus strength to both Data and Relic Analyzers. These ships also get an 7.5% (37.5% max) increase to scan strength per racial frigate level, which helps in finding hacking sites. | Each race's T1 Exploration frigate has an innate role bonus of 5+ virus strength to both Data and Relic Analyzers. These ships also get an 7.5% (37.5% max) increase to scan strength per racial frigate level, which helps in finding hacking sites. | ||
| Line 113: | Line 113: | ||
===Ship equipment=== | ===Ship equipment=== | ||
To do hacking you need either a Data Analyzer or Relic Analyzer, depending on the site. There are no relevant mid or low slot modules, but rigs are available to make hacking easier | To do hacking you need either a Data Analyzer or Relic Analyzer, depending on the site. There are no relevant mid or low slot modules, but rigs are available to make hacking easier. | ||
Full list of normally used scanning equipment: | Full list of normally used scanning equipment: | ||
Revision as of 21:27, 20 May 2020

|
| Exploration |
|---|
| Site types |
| Guides |
Hacking is used to access the items in relic sites, data sites and chemical labs.
Hacking minigame
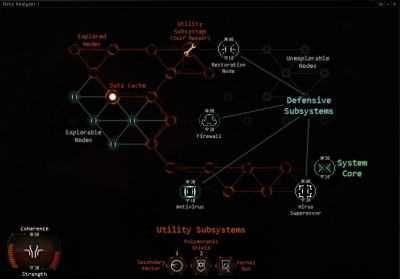
Mercifully, the hacking minigame is identical in all sites, aside from a few cosmetic changes to the game’s playfield and sound effects. The object of the hacking minigame is to find and disable the container’s System Core. You do this by maneuvering a virus through the board of “nodes” that represent the container’s electronics.
Moving around the board is easy enough. Unexplored nodes in the system are marked as green. Clicking on an unexplored node will reveal its contents: if the node is empty, it will turn orange and allow you to further explore nodes adjacent to it. Sometimes, however, a node will contain an obstacle or other item of interest.
Additionally, as you click on each node, if it is unoccupied (or after you clear the item from the node), it will briefly display a "minesweeper" number, from 1 to 5, which indicates the distance from the nearest non-empy node (5 means "5 or more".). This shows distance from any undiscovered Utility Subsystem, System Core, or Data Cache. The numbers can be used to guide the direction that you should move around the grid.
Among the various things a node may contain are...
Defensive Subsystems
These are represented by large circles with an icon inside, and they will be the bane of your hacking existence. Defensive Subsystems prevent you from exploring adjacent nodes until they are disabled. Each Defensive Subsystem has two ratings: Coherence represented by an asterisk atop the Subsystem, which is the equivalent of its health/HP, and Strength represented by a “wifi/signal” icon listed at the bottom of the Subsystem, which is equivalent to its “attack power.”
Your virus has a Coherence and Strength, too, which you can use to disable the system’s defenses! Your virus’s Coherence and Strength are listed in the bottom left of the hacking window. You can attack a Defensive Subsystem by clicking it after it has been explored. Attacking a Subsystem is turn-based: your virus will attack the Subsystem lowering the subsystem's Coherence by your Virus Strength, and then, if the Subsystem is still active, it will attack your virus back. If you reduce the subsystem's Coherence to 0, it is disabled and removed from the board.
If your Virus Coherence reaches 0, you fail the hack and the window is closed. Failing a hack once does not matter for regular Data/Relic sites, but failing a second hack will destroy that container. (Note that for some special kinds of containers/sites, such as Ghost Sites, Sleeper Caches, etc., failing the first hack might cause an explosion, or have other negative effects.). Interrupting a hack counts as a failure, and that includes moving too far away from the can (out of range of your analyzer) while the hacking window is open. This is sometimes a problem for frigates with a MicroWarpDrive active, where you can overshoot the can when Approaching it too fast - so be careful.

|
Firewalls have high coherence, but low strength. |

|
Anti-Virus subsystems have low coherence, but high strength. |

|
Restoration Nodes show up in more difficult hacks. Each turn they are active, they will give extra coherence to all other uncovered defensive subsystems. Incredibly nasty. |

|
Virus Suppressor subsystems lower your Virus Strength while active. |
| File:Core node1.png | Core is the target of hacking. Disabling it will complete the hack. The color of the System Core reflects the difficulty of the container: Green for easy; Orange for medium; Red for hard. |
Data Caches
Data Caches act a bit like a “treasure chest.” They can contain either a “treasure” (a useful Utility Subsystem), or a “trap” (a particularly nasty Defensive Subsystem). Data Caches have to be manually opened after being exposed (single-click them), so you can safely leave the decision as to whether or not to chance their activation until later on in your hacking attempt.
Utility Subsystems
Utility Subsystems are helpful, consumable “files” that have been left inside the system. You can click one once it has been exposed to add it to a utility slot at the bottom middle of your hacking window. They can then be used by clicking the appropriate utility slot. You can only store three Utility Subsystems at a time, so plan ahead!
Utility Subsystems are extremely useful and come in a few different types.
Thankfully, exploring until you find the System Core and then annihilating it isn’t too difficult in the vast majority of sites you will find in high-sec. With a little practice, you’ll be hacking with the best of them!
Skills
- Archaeology (3x, 250k ISK): Required skill for the use of Relic Analyzer modules. Gives +10 Virus Coherence per level.
- Relic Analyzers require Archaeology, and are a fairly cheap mid-slot module used to interact with structures found inside exploration-located Relic Sites. A good amount of your income as an explorer will come from accessing these structures, so note this skill's importance!
- Higher skill levels make the minigame associated with opening Relic Site structures easier, with Archaeology V allowing you to use the significantly-more-powerful Relic Analyzer II module. Any serious explorer should plan to eventually max this skill out, especially if you intend to do Relic sites in Nullsec or Wormholes.
- Hacking (3x, 250k ISK): Required skill for the use of Data Analyzer modules. Gives +10 Virus Coherence per level.
- A la Archaeology, Data Analyzers require Hacking, and open structures found in Data Sites. Hacking I has slightly higher requirements than Archaeology I, but make sure you get both skills, so that you can hack any sites you find.
- Also like Archaeology, higher skill levels make the Hacking minigame easier, and Hacking V will give you access to the Data Analyzer II module, which gives better bonuses, and is especially needed for Data sites in Nullsec or Wormholes.
Ships and equipment
Ships
Hacking can be done in any ship that has mid slots for Data and/or Relic Analyzers. However, there are ships with innate bonuses to hacking. These ships gain very helpful bonus to hacking module virus strength, the additional probe strength bonus helps with scanning. Nothing prevents you from doing hacking in other ships but unbonused hull places more weight on skills and knowledge.
Each race's T1 Exploration frigate has an innate role bonus of 5+ virus strength to both Data and Relic Analyzers. These ships also get an 7.5% (37.5% max) increase to scan strength per racial frigate level, which helps in finding hacking sites.
Covops ships are the direct upgrade from T1 scanning frigates. They get a +10 bonus to virus strength, +10% (50% max) per level bonus to scanning, and can use covert ops cloaking devices.
The Sisters of EVE faction ships all have a +10 bonus to Virus Strength (Same as Covops Ships), a 37.5% role bonus to scanning (Same as T1 Exploration Frigates), and the frigate and cruiser are also able to fit a Covert Ops cloak. They also get bonus to armor resists, energy turrets and drones making them capable combat crafts. They have lower skill requirements than CovOps T2's, but they are insanely expensive compared to other T1 ships and considerably more expensive than T2 ships.
 Astero Frigate. (CPU is low, making it hard to fit an Expanded Probe Launcher.)
Astero Frigate. (CPU is low, making it hard to fit an Expanded Probe Launcher.) Stratios Cruiser.
Stratios Cruiser. Nestor Battleship. Role Bonus: 50% bonus to Core and Combat Scanner Probe strength. Cannot fit a Covert Ops cloak.
Nestor Battleship. Role Bonus: 50% bonus to Core and Combat Scanner Probe strength. Cannot fit a Covert Ops cloak.
Strategic cruisers can be fitted with the Covert Reconfiguration subsystem that gives them 10% per level probing bonuses, +10 virus strength, and ability to use Covert Ops Cloak. If you're in a roaming gang of strategic cruisers, this might be useful -- but note that you can buy about 50 covops ships for the price of one of these.
Ship equipment
To do hacking you need either a Data Analyzer or Relic Analyzer, depending on the site. There are no relevant mid or low slot modules, but rigs are available to make hacking easier.
Full list of normally used scanning equipment:
| Data Analyzers are used to hack Data and Chemical Lab sites found while exploring.
The T1 module has a base 40 Virus Coherence and 20 Strength, with the T2 Version has an additional +20 Virus Coherence (60 total) and +10 Virus Strength (30 total) | |
| Relic Analyzers are only used to hack Relic Sites
The T1 module has a base 40 Virus Coherence and 20 Strength, with the T2 Version has an additional +20 Virus Coherence (60 total) and +10 Virus Strength (30 total) | |

|
Integrated Analyzers are single modules that can hack both Data and Relic sites. They are incredibly expensive compared to the individual analyzers, have lower Virus Coherence & Strength, and less Utility subsystem slots.
Integrated Analyzers will get bonus Coherence from both Archaeology and Hacking skills, alongside the bonuses from either rig listed below. |
| Memetic Algorithm Bank rig increases the virus coherence of both Data and Integrated Analyzers. the T1 rig increases the Coherence by +10, and the T2 version increases it by +20. Due to Calibration size and ISK cost, it is more cost-effective to have two T1 rigs than one T2 rig. | |
| Emission Scope Sharpener rig increases the virus coherence of both Relic and Integrated Analyzers. the T1 rig increases the Coherence by +10, and the T2 version increases it by +20. Due to Calibration size and ISK cost, it is more cost-effective to have two T1 rigs than one T2 rig. |
There also exist three slot 9 implants that improve hacking attributes. The implants apply their effect only to either relic or data analyzers but again the integrated analyzers receive these bonuses in all situations.
| Implant | Effect |
|---|---|
| Poteque 'Prospector' Archaeology AC-905 | +5 coherence for relic analyzers |
| Poteque 'Prospector' Hacking HC-905 | +5 coherence for data analyzers |
| Neural Lace 'Blackglass' Net Intrusion 920-40 | -40 coherence for data analyzers +20 strength for data analyzers |
The slot 10 EY-1005 implant improves virus coherence for both relic and data analyzers.
| Implant | Effect |
|---|---|
| Poteque 'Prospector' Environmental Analysis EY-1005 | +5 coherence for data and relic analyzers |
Tips and Tricks
- As a general rule, you’ll want to explore as many nodes as you can before attacking any static Defensive Subsystems. In general, it’s better to explore the entire board before engaging with any subsystems: you may just stumble onto the System Core early! Restoration Nodes and Virus Suppressors are the exception to this though, as they should be removed from the board as soon as possible.
- Always pick up Utility Subsystems as soon as they are exposed. If you keep exploring without snagging these, a Defensive Subsystem might pop up and cut off your access to them!
- Always use a Self Repair as soon as you find it. It simply increases your Coherence, so there is no gain in waiting.
- Don’t open Data Caches until you’ve fully explored all their adjacent nodes. You don’t want your exploration to be cut off by an unexpected Defensive Subsystem!
- Additionally, more difficult hacks contain Data Caches that might expose particularly nasty Defensive Subsystems (Restoration Nodes), so sometimes, you may just want to leave opening Data Caches as a last resort.
- Because exposed Defensive Subsystems cut off access to adjacent nodes, you may want to explore nodes along the edges first before exploring inward. This is because if you happen to expose a Firewall or Anti-Virus along a “wall,” you will be a bit less likely to cut off all of your movement options in that direction.
- Use the 1-5 "minesweeper" numbers to guide your movement around the grid. For example, if you're approaching an edge or corner of the grid, and the number is a 5, then trying to explore anything towards that corner/edge is not useful, because you know that there cannot be anything good within 5 nodes. In general, you want to click in directions that make the numbers smaller. Because the numbers disappear as you move along, you need to remember where there were 5's, so you know which areas not to bother going back to later.
- Use the Rule of Six. This rule is slightly complicated, but can make your life when hacking much easier. The rule is that if you have a node that has six edges leading away from it ( a "complete" node with no missing nodes in the hexagon around it), then that node is guaranteed to 1) Have no Defensive Subsystems in it OR 2) be adjacent to the System Core. What that means in practice is that you can use these squares to move safely through the board, and any Defensive Subsystems you find tell you where the System Core is. It is usually worthwhile to try to reach and use areas of the map with many of these "complete" nodes when hacking. You can find a video tutorial here.




